Secure web scraping has evolved from a purely technical task to a critical component of enterprise security infrastructure. For years, web data extraction involved simple scripts, proxies, and IP rotation. Today, however, that view is obsolete. Modern compliant data extraction directly impacts compliance, operational risk, and corporate reputation.
At Scraping Pros, we have spent nearly a decade working with global organizations that depend on external data flows to operate. Our experience has led us to a clear conclusion: secure scraping requires architecture, governance, and observability. This article is written for CISOs, security leaders, and compliance officers who need to transform data extraction into a controlled asset rather than a silent risk.
1. The New Perimeter: Why Scraping Is Now a CISO-Suite Issue
The traditional security perimeter has become blurred. APIs, SaaS integrations, third-party providers, and automation have expanded the attack surface. Scraping has been added to that list, but many organizations still don’t recognize it as such.
Today, extraction pipelines:
- Handle technical identities.
- Operate from distributed infrastructures.
- Interact with uncontrolled external systems.
- Generate traffic that can be indistinguishable from automated abuse.
From a CISO’s perspective, this implies risk. Not because scraping is illegal or inherently dangerous, but because without security controls, it behaves like an “ungoverned third system”.
At Scraping Pros, we see this daily: business teams launch critical scrapers without visibility for Security. The result is usually not an immediate incident, but something more insidious: mass lockouts, indirect exposure of credentials, abuse alerts, or negative audit findings.
That’s why we talk about Zero-Trust Scraping: no extraction process should be trusted by default, even if it’s internal.
2. The 2025 Risk Landscape: Data, Gaps, and Real Costs
During technical audits, we analyze enterprise scraping infrastructures and find that the patterns are repeated:
- Between 17% and 23% of technical credential exposure incidents are related to non-isolated automations.
- 31% of audited pipelines reuse identities or tokens beyond their original scope.
- Nearly 40% of medium and large companies have undisclosed “shadow” scrapers.
The impact isn’t always a classic breach. Often, it translates into:
- Persistent blocks by anti-bot systems.
- Degradation of data quality.
- Escalating infrastructure costs.
- Reputational risk with third parties.
However, when secure scraping best practices are applied, the numbers change:
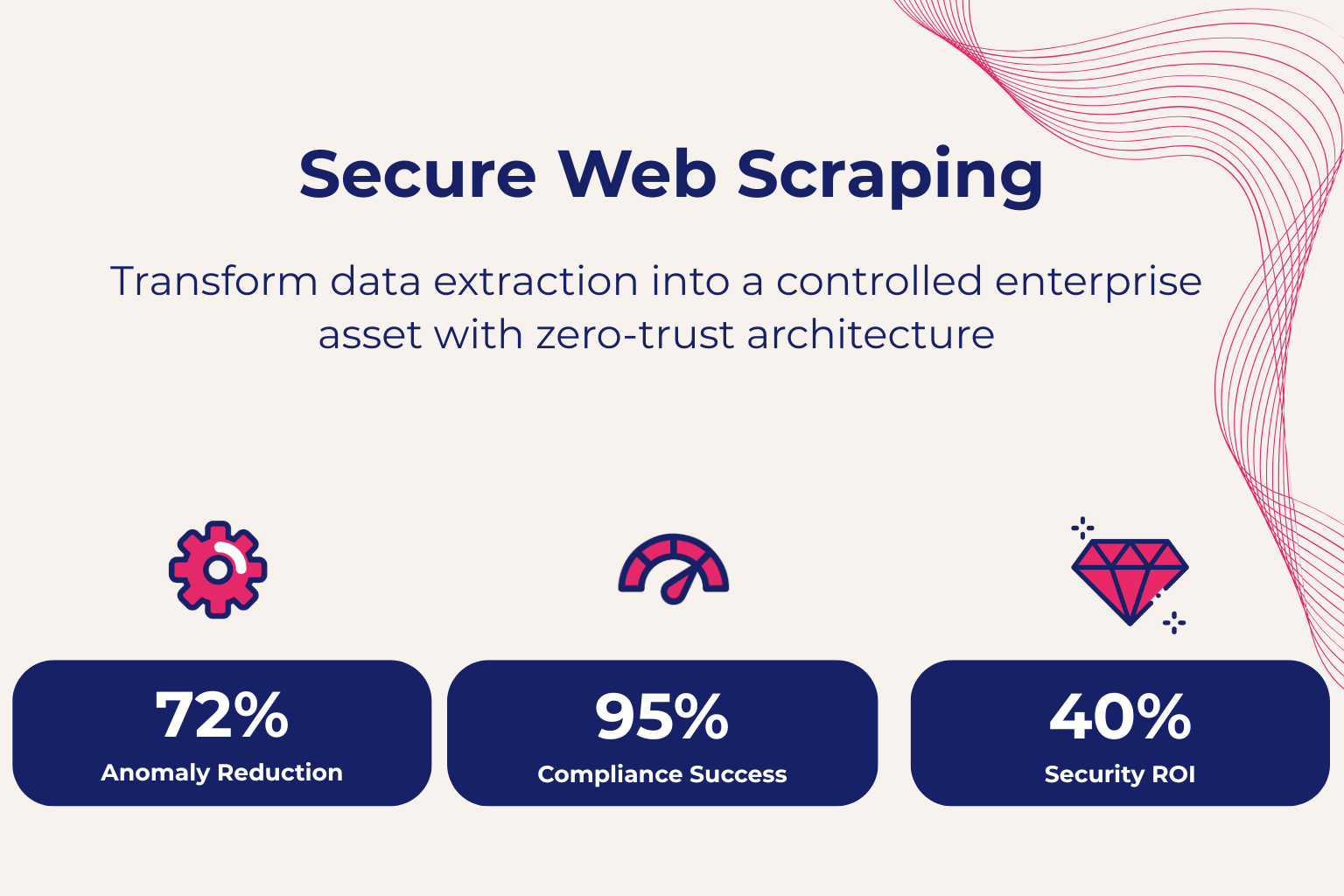
- Up to a 72% reduction in traffic anomalies.
- A 95% success rate in compliance audits related to data extraction.
- A 30–40% security ROI by reducing incidents and rework.
Scraping Pros uses these indicators as operational metrics, not theory. Secure web scraping is measurable and reduces friction, speeding up internal approvals.
3. Compliance-Driven Scraping: Complying Without Slowing Down Business
One of the most common mistakes is treating compliance as a technical constraint. In reality, the problem is usually architectural.
At Scraping Pros, we use an approach called Compliance-Embedded Extraction (CEE). With CEE, compliance is integrated from the design stage, not validated at the end.
This involves clearly separating three layers:
A) Legal
Definition of legitimate basis, documented purpose of data use, and temporal and jurisdictional scope.
B) Technical
Data minimization from the source, early pseudonymization, and removal of unnecessary fields before storage.
C) Operational
Auditable logs, pipeline versioning, and reproducible evidence for audits.
One key point that many organizations overlook is that not all restrictions are access restrictions. Many are usage restrictions. Designing compliant data extraction with this distinction in mind reduces friction and speeds up internal approvals.
4. Secure Scraping Architecture: The Blueprint a CISO Should Demand
Enterprise scraping isn’t solved with “better scripts.” It’s solved with architecture.
At Scraping Pros, we design extraction infrastructures with clear components:
- Scraping nodes with isolated identities, preventing correlation and reuse.
- Network segmentation and end-to-end encrypted tunnels.
- Consistent, not random, fingerprinting protection.
- Data governance pipeline, integrated with DLP and SIEM.
- Integrity channels to ensure data is not altered in transit.
This approach allows for something fundamental: the CISO can explain and defend scraping to auditors, regulators, or the board of directors. Not as a black box, but as a controlled system.
5. The “Compliance Firewall”: An Ignored Technical Layer
A concept we are increasingly applying is that of the Compliance Firewall: an intermediate layer between the scraper and the final storage.
This firewall allows for the redaction or discarding of sensitive data in real time, the application of rules by jurisdiction, and the blocking of unauthorized uses before the data even exists as an asset.
In practical terms, it reduces legal risk even if the scraping itself is legitimate. For CISOs, this means defense in depth applied to external data.
6. Observability and Forensics: Making the Invisible Visible
A scraper without observability is a latent risk. Modern scraping pros’ infrastructures integrate with:
- Enterprise SIEMs.
- Anomaly detection systems.
- Immutable forensic logs.
This allows for the detection of:
- Fingerprint drift.
- Anomalous changes in behavior.
- Misuse of technical identities.
The key is to treat scraping like any other critical system: if it can’t be audited, it can’t be secured.
7. Governance: Translating Scraping into Business Language
For scraping to be sustainable, a clear governance framework is essential:
- Defined Ownership.
- Documented Data Lifecycle.
- Regular Audits.
- Executive Metrics.
At Scraping Pros, we help organizations build indicators such as:
- Compliance Audit Success Rate.
- Scraper Reliability Index.
- Risk Reduction Percentage per Pipeline.
This translates technical complexity into business language.
8. 90-Day Roadmap for CISOs
A typical approach we recommend:
Phase 1 – Discover and Stabilize
- Inventory scrapers.
- Identify shadow scraping.
- Classify risks.
Phase 2 – Secure and Govern
- Implement Zero-Trust Scraping.
- Integrate with SIEM and compliance.
- Document uses and purposes.
Phase 3 – Scale and Optimize
- Automate controls.
- Measure risk reduction.
- Prepare for ongoing audits.
Scraping Pros typically supports this process from start to finish, not as a one-off vendor, but as a technical partner.
Conclusion: The New Normal of Enterprise Scraping
Scraping is not just a problem for the technical team anymore. It’s also a matter of security, compliance, and business strategy.
Organizations that understand this early on will:
- Reduce risks.
- Improve data quality.
- Gain speed without sacrificing control.
At Scraping Pros, we build infrastructures designed for this new scenario. They are secure, auditable, and aligned with the real demands of 2025. The future of scraping isn’t more aggressive. It’s more secure, transparent, and governed well.
Interested in transforming your company with this perspective? Contact our executives free of charge.
FAQs
1. What is secure web scraping in an enterprise context?
Secure web scraping in an enterprise context refers to extracting publicly available or permitted web data using controlled architectures that enforce security, compliance, and governance. It includes identity isolation, encrypted traffic, audit logs, data minimization, and continuous monitoring. At Scraping Pros, secure web scraping is treated as part of the organization’s security perimeter, not as an ad-hoc automation task.
2. Is web scraping compliant with GDPR, CCPA, and data protection regulations?
Yes, web scraping can be compliant with GDPR, CCPA, and other data protection frameworks when it follows privacy-by-design principles. This includes limiting data collection to defined purposes, avoiding unnecessary personal data, applying anonymization or pseudonymization, and maintaining auditable logs. Scraping Pros embeds compliance controls directly into scraping architectures to ensure regulatory alignment from day one.
3. Why do CISOs consider web scraping a security risk?
CISOs consider web scraping a risk when it operates outside security governance. Uncontrolled scrapers can expose credentials, generate abnormal traffic patterns, violate third-party terms, or fail compliance audits. Secure scraping architectures mitigate these risks by applying zero-trust principles, segmented infrastructure, and full observability across all data extraction workflows.
4. How does secure scraping differ from traditional web scraping?
Traditional web scraping focuses on data acquisition speed and scale, often ignoring security and compliance. Secure web scraping prioritizes controlled identities, encrypted communication, compliance firewalls, and monitoring. Scraping Pros designs scraping systems that balance data access with enterprise-grade security, reducing legal, operational, and reputational risk.
5. Can web scraping be integrated with enterprise security tools like SIEM or DLP?
Yes. Modern scraping infrastructures can and should integrate with SIEM, DLP, and monitoring platforms. This allows security teams to detect anomalies, track data flows, and audit extraction activity. Scraping Pros routinely integrates scraping pipelines into existing enterprise security stacks to ensure full visibility and incident response readiness.
6. When should a company work with a specialized scraping provider like Scraping Pros?
Companies should work with a specialized provider when web scraping becomes mission-critical, regulated, or high-risk. This includes financial services, large-scale market intelligence, or compliance-sensitive environments. Scraping Pros provides secure, compliant data extraction architectures designed for global enterprise use cases.
Security is built into our service
GDPR/CCPA compliant with enterprise-grade data protection. We handle security so your team doesn’t have to worry about compliance risks.

